蜀道山CTF-PWN全解WP
蜀道山CTF-PWN附件下载:https://z-l-s-f.lanzouq.com/ixEZc2g31zdg
one_heap
check:
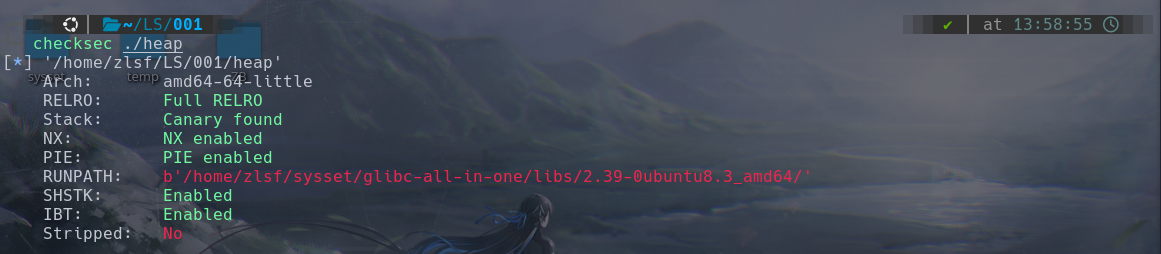
题目保护全开
漏洞点:
1.

uaf漏洞。
2.
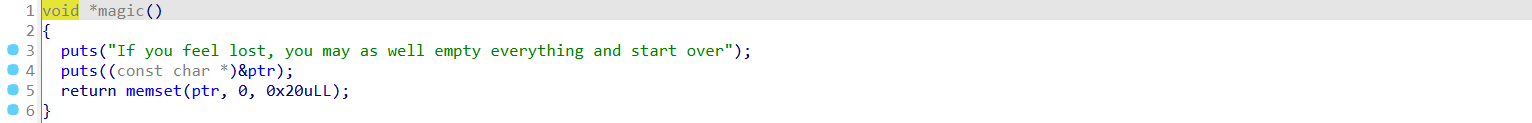
输出指向当前堆块的地址(而非堆块的内容)。
思路:
题目只允许一次操作一个堆块,但是我们可以通过magic函数来造成tcachebin的uaf,释放任意一堆块获得heap的基地址,通过tcatche的uaf申请到tcachebin的开头(也就是堆块的起始地址这个位置,这里记录了tcache堆块的所有信息,我们可以修改这个地方影响tcachebin的行为)。
通过修改堆块0x290的数量为7,释放tcachebin头进入unsortbins,此时堆中出现了libc的地址,申请合适的堆块来让这个libc地址到0x100的范围中,通过申请0xF8可以将堆块申请到这个libc地址上(不能将unsortbin构造到其他地址是因为高libc版本会有加密,加密后申请是必不会成功的)。
通过magic输出libc的地址后可得libc的基地址。
通过正常的tcachebin attack劫持_IO_list_all到堆中打house of apple2即可完成攻击。
exp:
1 | |
small stmashing
check:
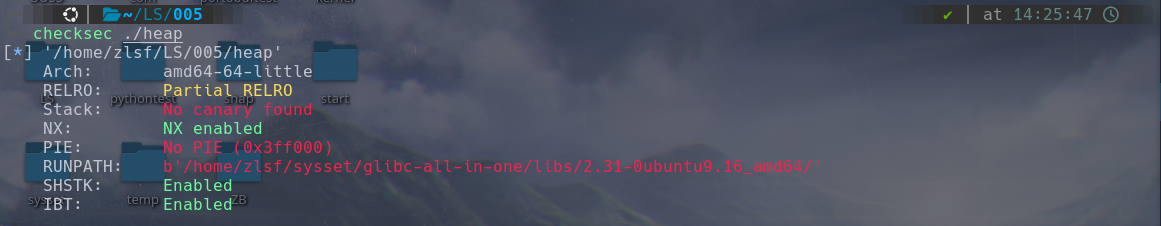
沙盒:
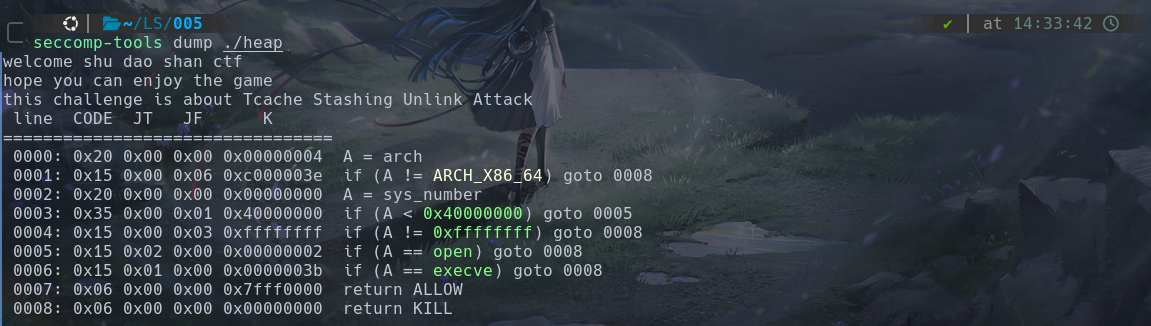
NX保护开启,RELRO半开。
漏洞点:
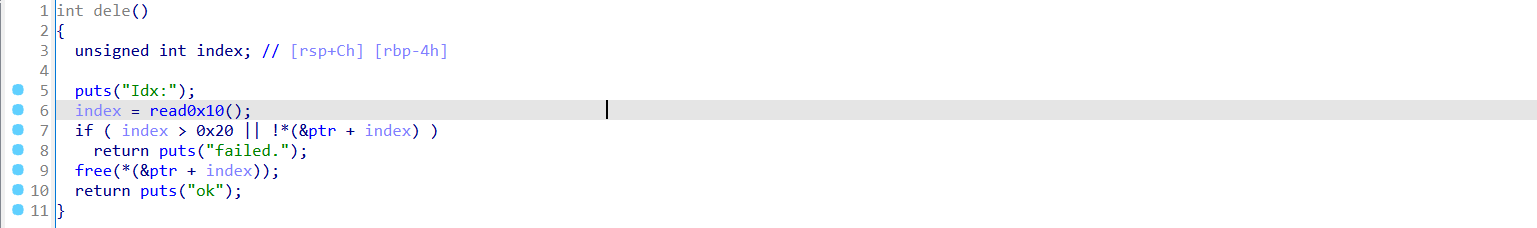
存在uaf漏洞。
思路:
我们最多可以持有33个堆块,我们只能持有0x78到0x3F8之间的堆块。
add函数使用了calloc,该函数的特点就是不会从tcachebins中获取堆块。
我们先通过9次申请0x288然后再释放,此时会有unsortbins出现,我们可以同时获得堆基地址(add函数会输出堆地址)和libc基地址。
题目的本意应该是要我们使用smallbin中的attack,但是我们可以非常极限的通过大量的堆块来完成largebin attack(因为选择5有一个可选栈溢出,通过largebin attack到0x4040C0可以获得大量的输入来构造ORW)。
通过非常规方法构造largebin attack非常麻烦。
1.你得先构造两个0x500~0x530的largebin范围的unsortbin,和一个至少小于0x500的unsortbin,此时他们都不是释放状态。
2.此时先释放0x520的块到unsorbin中,然后释放小于0x500的块到unsortbin中,申请一个和你组成unsortbin堆块大小无关的堆块(比如我是通过0x288和0x88凭凑的,就可以申请0x98),此时会从小于0x500的unsortbin分割出0x98的堆块,而0x520的堆块会被释放到largebin中。
3.再释放0x510的堆块到unsortbin中,伪造0x520的堆块的bk_nextsize = target - 0x20,此时再次申请0x98的堆块,我们就完成了largebin attack。
通过5号函数的栈溢出即可完成ORW。
exp:
1 | |
mini_notebook
check:
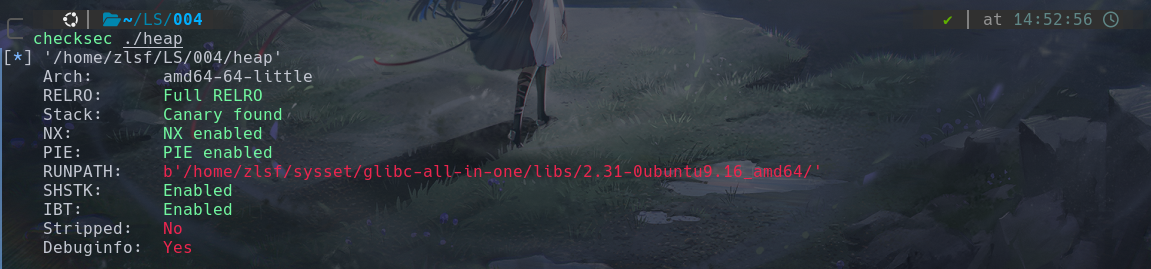
保护全开
漏洞点:
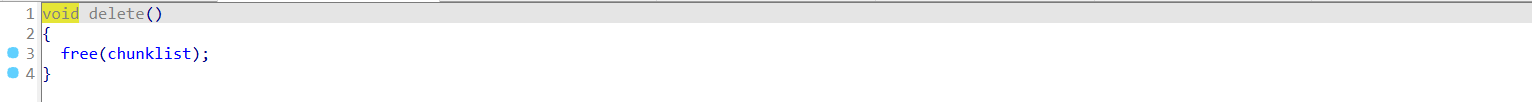
uaf漏洞。
思路:
通过tcache的double free打tcache头暴露libc基地址,然后打malloc_hook。
exp:
1 | |
no_leak_heap
check:
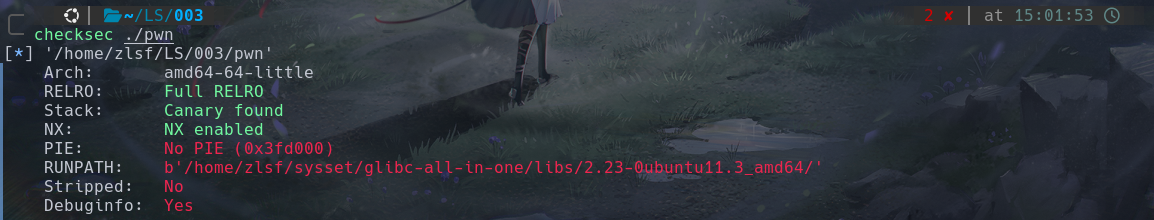
除了PIE其他保护全开。
漏洞点:
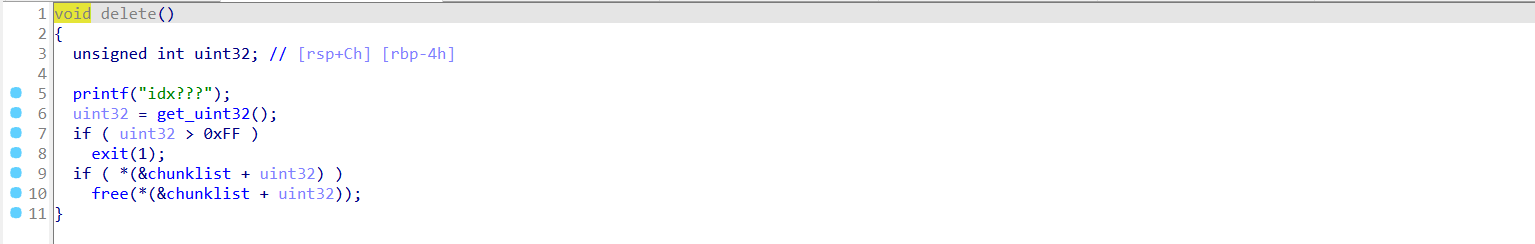
存在uaf漏洞。
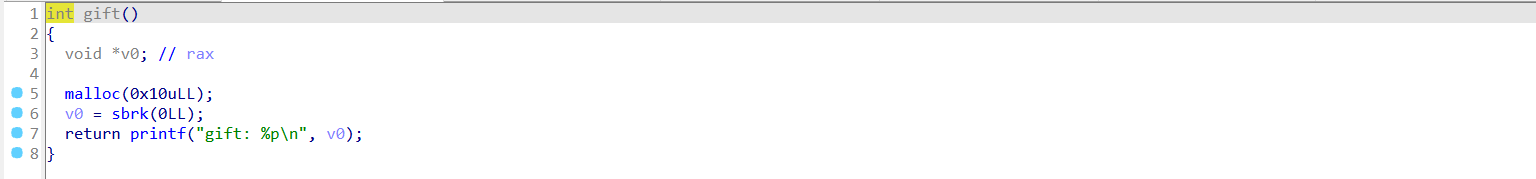
主动泄露堆地址。
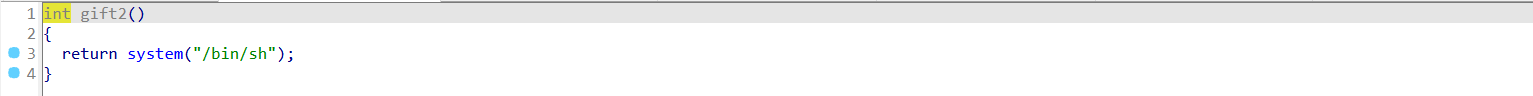
后门函数。
思路:
通过申请大块在堆块上残留libc地址,改其末尾为0x4aed申请到malloc_hook上,修改malloc_hook到后门完成getshell。
exp:
1 | |
mixian
check:
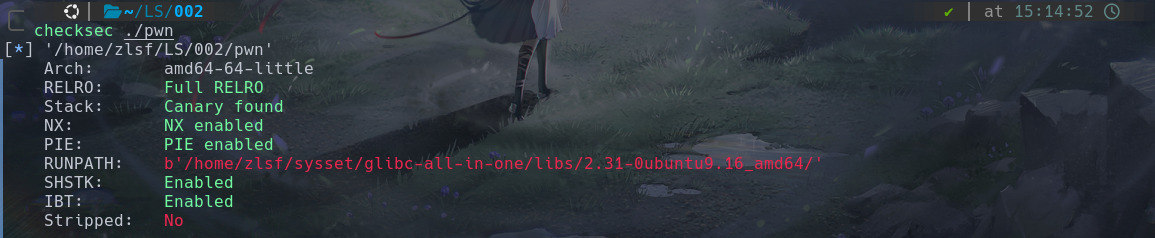
保护全开。
漏洞点:

num可以为负数,我们可以申请question_list到stdout的位置,修改stdou为经典的IO_FILE attck获得libc基地址。
num设置为3则正好可以修改最终判断的变量,通过libc基地址算出puts的地址加上rand()%0x2333的值就能完成getshell。
exp:
1 | |